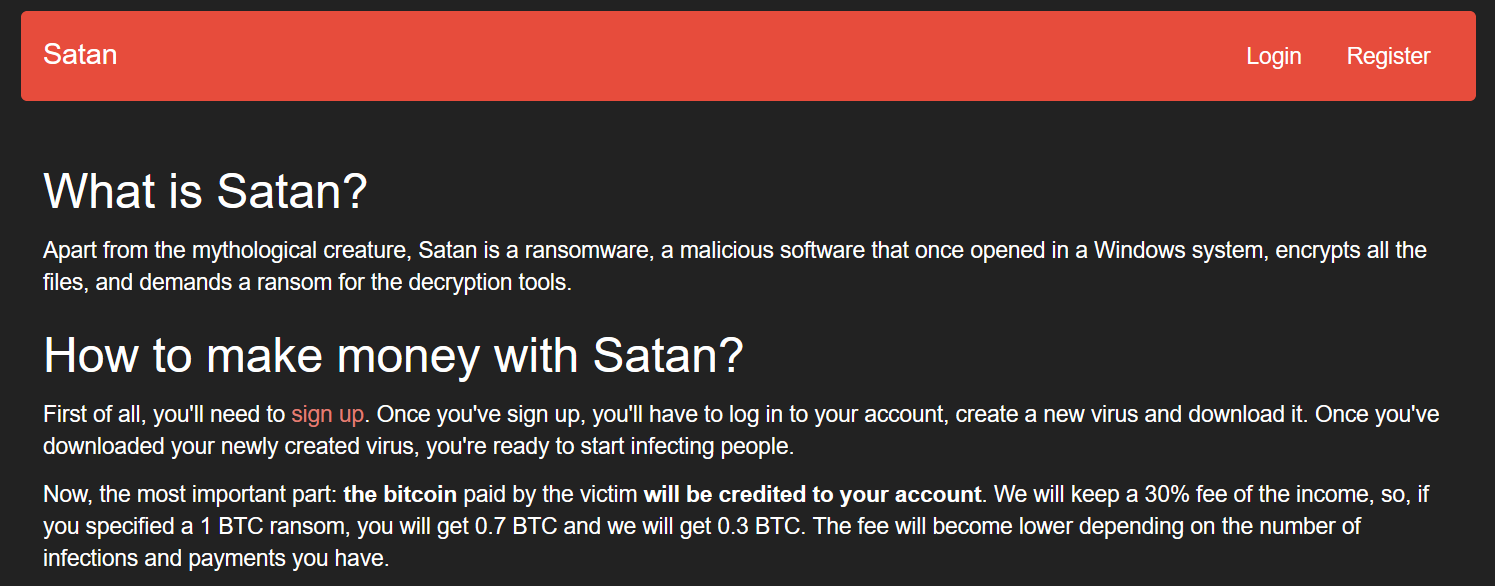
Ransomware as a Service (RAAS) Overview
Just like you can go out and run your website on a Infrastructure as a Service platform or use a popular CRM system (rhymes with Gale’s Horse) that is referred to as Software as a Service, threat actors can get malware from platforms offering Ransomware as a Service, complete with customization, obfuscation, packing, a billing service so that the hacker and the RAAS folks get paid on ransom collections.
Let’s look at this threat and discuss some ideas about how it impacts organizations and what some of the implications may be as they relate to improving cyber security controls and the Endpoint Security and Threat Management & Intelligence product markets.
Ease of Access & Use
Some of the RAAS tools available are so simple to use, your grandma could create her own ransomware campaign and start bringing in money.
Obfuscation and packing tools like Aegis Crypter make the malware more difficult to detect and increase the likelihood that the threat actor will attain his objective. With a well-planned and executed delivery and propagation mechanism, the attacker has the potential of infecting 10s or 100s of thousands of computers before the big box anti-malware vendors push out detection for his shiny new ransomware.
This point-and-click easy access to custom ransomware and the low barrier to entry makes RAAS tools very popular to threat actors in the cyber underground, whether they are highly skilled with a well-planned campaign objective or amateurs looking for some quick glory.
Implications
As RAAS systems become more widely used, as they are enhanced in terms of the ability to generate, package, and obfuscate new ransomware, and as the speed and efficiency with which threat actors can deliver the malware at scale, improvements will be needed in Endpoint Security and Threat Management & Intelligence tools that lower the Mean Time to Detection and Mean Time to Response to keep pace.
The need to detect and respond much more quickly may likely drive the market more toward products and solutions that use Artificial Intelligence and Machine Learning as key components, either as a replacement for or augmentation to solutions and products that use signatures and heuristics as a primary means of detection.
There is certainly a big push toward threat intelligence sharing and “collaboration” in some of the more comprehensive solution sets, such as what Sophos delivers with their Synchronized Security offering. This market sector will continue to grow and brings a lot of needed automated capabilities for detecting, containing, and mitigating threats of various kinds.
Detection & Prevention
Your information security controls should adapt with developments in attacker tools and techniques if you want to have a chance at defending against ransomware and other threats. Continuous adaptation means employing the latest technologies, processes, and methods to apply what we at Legion Cyberworks define as the Top 10 Security Essentials. These essential security controls were chosen as our Top 10 because they have been proven to be effective at preventing intrusions.
In addition to the Top 10 Security Essentials, your organization needs a SEIM and Threat Management & Intelligence platform or a Managed Security Services Provider that makes it possible to rapidly identify, qualify, and target active threats, and respond appropriately 24×7.
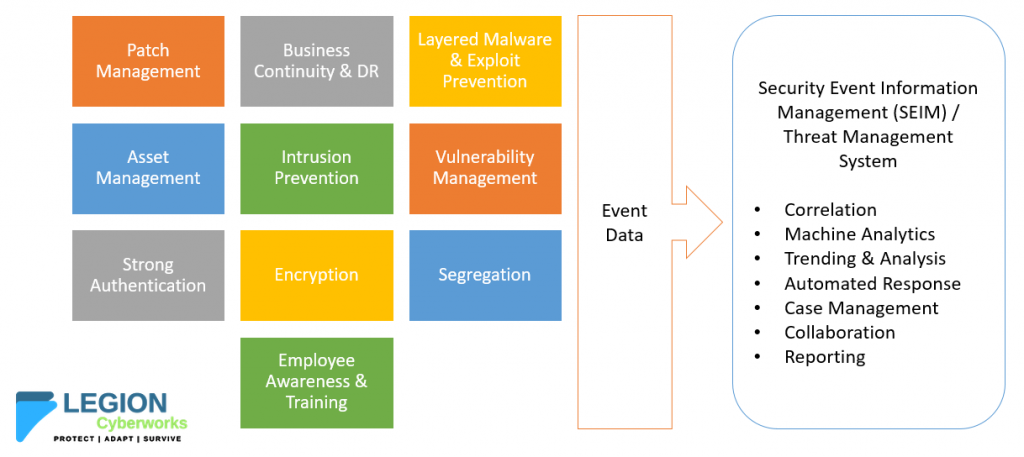
Combining these essential technical and administrative controls with a real-time view of threat activities will increase the likelihood that you will spot a real attack and be able to act before a breach occurs.
Using a well-designed security controls framework such as the CIS 20 Critical Controls for Effective Cyber Defense, or the NIST Framework will hit our Top 10 Security Essentials and more, and will give your organization some solid guidance on how to develop your own information security controls.
Wrap-Up
Disrupting and defeating the enemy will always require diligence and advancements in security technologies and how we use them. There are some very exciting solutions already on the market that leverage AI and Machine Learning which could be very effective elements of a comprehensive cyber defense system, and developments in these fields will continue to enhance cyber-defense capabilities.
Security Governance is also essential to supporting the ground-level battles in our SOCs. An agile, risk-based information security program ensures that the appropriate technology, process, and procedural changes are made to be able to protect, adapt, and survive as the threats and attacks change.
Contact us at [email protected] if you are interested in learning about how we can partner with you to improve your security posture.