Our rapid pentesting service delivers advanced security through autonomous AI-driven technology that simulates real world attacker behavior, uses the same TTPs as threat actors, and allows us to deliver a high quality pentest covering your internal infrastructure in 1-3 days in most cases.
- Complete your pentest requirements in days, not weeks.
- Let’s you see all the details – the path, proof, and fix-action recommendations so you can focus on remediation.
- Evaluate your security operations and controls through detailed pentest action logs, showing you everything we did.
- We show you the severity and proof of exploit so that you can fix what really matters and protect your business.
- We deliver as a one-time operation or you can subscribe to monthly or quarterly pentests.
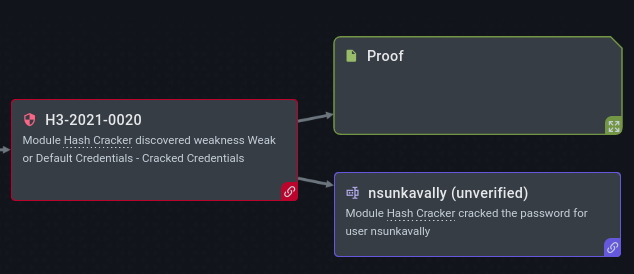
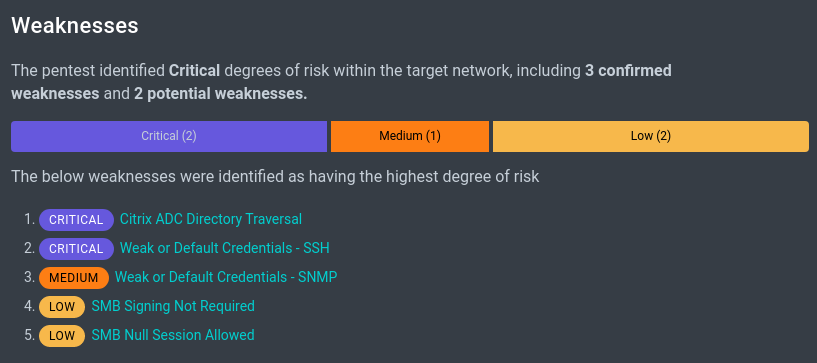
Ever wonder how much of your time and effort is being wasted fixing things that don’t actually matter?
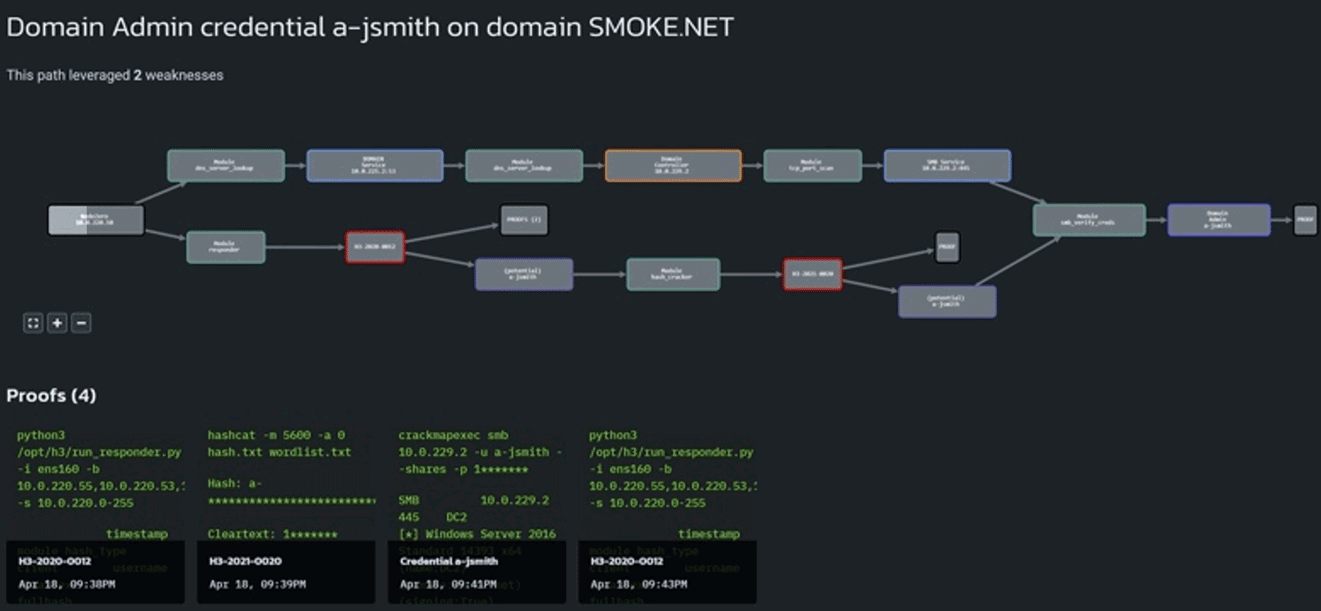
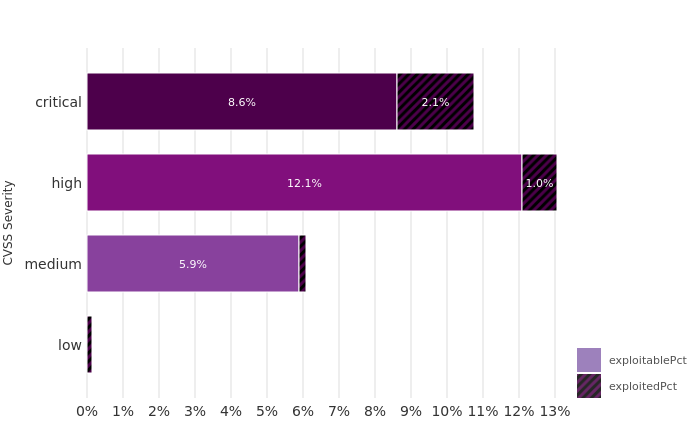
Criticality is a Function of Exploitability and Impact
The hardest part of cyber security is deciding what not to do because of limited time and resources. Spending valuable and scarce time and effort on remediating weaknesses that are not exploitable or do not represent a substantial business impact is itself a risk. At the very least, you should be able to trust that the findings from your security tools and services will appropriately guide your remediation and staffing decisions.

Get your required annual and semi-annual penetration testing in days, not weeks with our Rapid Pentesting Service
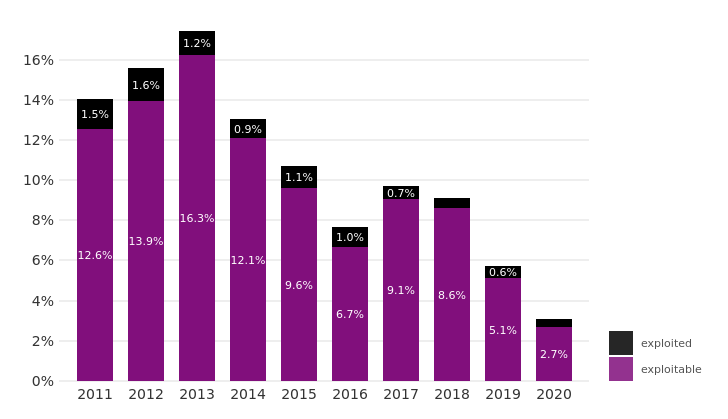
The number of CVEs disclosed has increased significantly in the last decade
The number of new CVEs published annually has increased over three-fold since 2011. This trend has accelerated since the expansion of the CVE Numbering Authority program in the last few years.
…yet the proportion of distinct vulnerabilities exploited is falling…
Although the known universe of vulnerabilities is exploding, an increasingly small number of those vulnerabilities result in actual breaches. Focusing your remediation efforts on high-impact mitigations has never been more important.
Above graphs and research are courtesy of Kenna Research – https://www.kennaresearch.com/a-decade-of-insights/
