In today’s digital landscape, cybersecurity threats are becoming increasingly sophisticated and targeted. For example, a client of ours experienced a spear phishing attack where an employee was targeted by a cybercriminal who tried to get her to run a malicious executable disguised as a Zoom updater. Fortunately, the cybersecurity controls and restrictions in place on her laptop did not allow her to execute the malware. Had these not been in place, this could have been devastating to their business. This incident serves as a stark reminder of the dangers that spear phishing poses to businesses of all sizes.
What is Spear Phishing?
Spear phishing is a type of cyberattack that targets specific individuals or organizations with the aim of stealing sensitive information. Unlike generic phishing attacks that cast a wide net, spear phishing is highly personalized, often exploiting information about the victim to make the attack appear more legitimate.
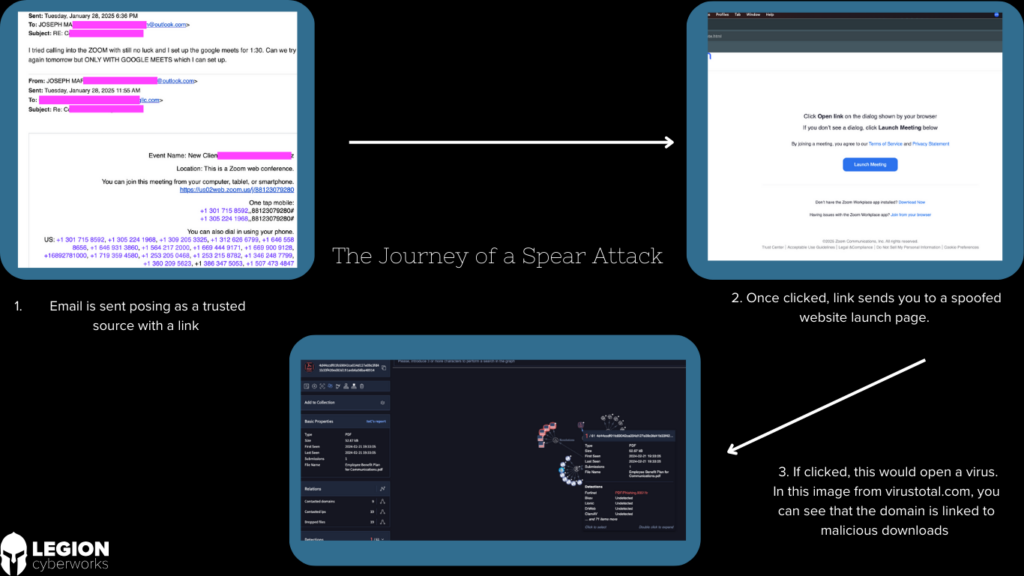
In the graphic above, you can see the journey that our client went on. This is a clear demonstration, of how an otherwise innocuous email can lead you to a virus and breach if not caught.
How Spear Phishing Works
Spear phishing can take various forms, with each method designed to deceive the target in different ways. Here are some of the most common techniques used by attackers:
- Impersonation: In this method, the attacker impersonates a high-ranking executive, department head, or other trusted authority figure to trick the victim into revealing confidential information or executing a malicious action.
- Clone Phishing: The attacker sends a fake email that closely resembles a legitimate one but includes a malicious link or attachment. For example, the attacker might send an email that appears to be a Zoom meeting update, but it contains a link to malware instead of a legitimate update.
- Brand Impersonation: Cybercriminals may also impersonate trusted brands, such as Microsoft or Google, to lure victims into clicking on malicious links or downloading harmful attachments.
- Vishing (Voice Phishing): Vishing involves an attacker calling the victim or leaving a voicemail pretending to be from a trusted entity, such as a bank or credit card company, in an attempt to steal personal information.
The primary goal of a spear phishing attack is to deceive the victim into providing access to sensitive data or systems. This could range from login credentials to financial information or access to proprietary business systems. In some cases, attackers may use this information for financial gain, data theft, or further infiltration into the victim’s network.
Attackers also use spear phishing as a way to deploy malware, remote access tools, and other malicious code that gives them a foothold in the network, or allows them to begin exfiltrating data before deploying ransomware.
How to Defend Against Spear Phishing
While spear phishing attacks are sophisticated, there are several proactive steps you can take to protect your organization:
- Partner with an MSSP: Managed Security Service Providers (MSSPs) like Legion Cyberworks specialize in detecting and mitigating advanced cybersecurity threats, including spear phishing. A trusted MSSP can provide the right expertise and tools to help safeguard your business from these types of attacks.
- Endpoint Detection and Response (EDR): Implementing EDR solutions can provide real-time monitoring of your endpoints, allowing you to detect and respond to suspicious activity before it escalates into a major security breach.
- Security Awareness Training: One of the most effective defenses against spear phishing is educating your employees about the risks and signs of phishing attacks. Regular training sessions can help them recognize suspicious emails, fake websites, and other red flags.
- Web Filtering: Use web filtering tools to block access to malicious websites that might be used for phishing or malware distribution.
- Email Filtering: Advanced email filtering can help catch malicious emails before they reach employees’ inboxes, reducing the chances of a successful phishing attempt.
- DNS Filtering: Filtering DNS queries adds a powerful prevention and detection layer to your security posture, often resulting in blocking malicious traffic before a connection is established between your environment and the threat actor.
- MXDR: Managed Extended Detection and Response (MXDR) provides a multi-layered approach to threat detection and response. By integrating various security tools and services, MXDR offers a comprehensive defense against phishing and other advanced threats.
Legion Cyberworks Can Help
At Legion Cyberworks, we specialize in providing advanced cybersecurity solutions to protect your business from evolving threats like spear phishing. As a trusted MSSP, we offer a comprehensive cyber stack built on leading technologies such as Guardz, SentinelOne, and Todyl. These tools work together to deliver a multi-layered defense against sophisticated cyberattacks. If your organization isn’t yet using a robust cybersecurity solution, now is the time to implement these critical protections. Partnering with us ensures that your business is safeguarded from spear phishing and other growing cyber threats. Contact us today to learn how we can help strengthen your cybersecurity defenses.

