Recent Threat Highlights
| Critical | CVE-2022-23277 | Microsoft Exchange Server Remote Code Execution Vulnerability- CVE-2022-23277 is a critical RCE vulnerability in Microsoft Exchange Server. An authenticated user can exploit this vulnerability to execute arbitrary code on an affected server. According to Microsoft’s Exploitability Index rating, this vulnerability is rated Exploitation More Likely | |||
| High | CVE-2022-24508 | Windows SMBv3 Client/Server Remote Code Execution Vulnerability- CVE-2022-24508 is a RCE vulnerability in the Microsoft Server Message Block 3.0 (SMBv3) Client and Server. Microsoft notes that this vulnerability was introduced in Windows 10 version 2004 so only newer supported versions of Windows are affected.
CVE-2022-24459 | Windows Fax and Scan Service Elevation of Privilege Vulnerability- CVE-2022-24459 is a privilege escalation vulnerability affecting the Windows Fax and Scan service. The vulnerability carries a CVSSv3 score of 7.8 and can be exploited by a local, authenticated attacker. |
|||
Cyber Intel by Industry
| Cyber / MSP / MSSP | Emotet Malware- Emotet has taken over as the most popular malware used this month. Emotet is an advanced, self-propagating and modular Trojan. Emotet, once used as a banking Trojan, has recently been used as a distributor to other malware or malicious campaigns. It uses multiple methods for maintaining persistence and evasion techniques to avoid detection. In addition, it can be spread through phishing spam emails containing malicious attachments or links.
Emotet is an advanced, self-propagating and modular Trojan. Emotet, once used as a banking Trojan, has recently been used as a distributor to other malware or malicious campaigns. It uses multiple methods for maintaining persistence and evasion techniques to avoid detection. In addition, it can be spread through phishing spam emails containing malicious attachments or links. |
|||
| Healthcare | Cynerio, a leading provider of healthcare IoT cybersecurity, today announced the company will debut Active Attack Detection at ViVE and HIMSS 2022, a new solution to empower hospitals and healthcare facilities to identify ongoing IoT attacks. In just one week, Cynerio's Active Attack Detection technology identifies attacks not found by legacy systems due to increasingly targeted IoT devices – at no cost to hospitals | |||
| SaaS Providers | Analysis of security events across more than 120,000 user accounts last year shows that the vast majority of attacks on top SaaS platforms such as Microsoft 365, Google Workspace, Slack and Dropbox are coming from Russia and China.The latest SaaS Application Security Insights (SASI) Report from SaaS Alerts also suggests these countries may be coordinating attack efforts.
Attack trend lines that compare Russia and China show almost exactly the same pattern. On average, SaaS Alerts is seeing approximately 10,000 brute force attacks each day against the user accounts monitored. The origin of potential attacks can be traced back to specific countries with current data indicating that attempted unauthorized logins are coming from actors located in China, Vietnam, Russia, Korea and Brazil. We expect to see a continued increase in attacks from Russia as the Ukraine situation escalates. |
|||
| Financial Services | Police are urging Hawaii banks, businesses and government institutions to see if a hacking suspect was spotted on their surveillance video. Kobina Nyarku, 30, has been charged with two felonies for allegedly hacking into Central Pacific Bank’s computer system. Police said he pretended to apply for a job at the bank at one of their computer terminals and was able to get access to their system to obtain information on employees. He was arrested last week during a fake interview set up by the bank. | |||
| IT Infrastructure & Hardware Manufacturers | American colossus Nvidia has been fending off a massive cyber attack for several weeks now, and Korean giant Samsung recently divulged that it has been targeted by the same group of hackers. The Lapsus$ ransomware group claimed responsibility for the Nvidia breach last week, and its demands became increasingly high-stakes as the company neared the hackers' March 4 deadline.
https://www.thestreet.com/technology/seeing-more-spam-phishing-or-malware-ask-nvidia-and-samsung |
|||
| Government | Darktrace, a global leader in cyber security AI, today announced Darktrace Federal, a new division to serve the U.S. Department of Defense (DoD), the intelligence community, federal civilian agencies, and national critical infrastructure to strengthen their defenses with Self-Learning AI. | |||
Weekly Honeypot Stats
The following are curated from our network of honeypots which are exposed to Internet traffic. Legion Cyberworks uses our network of honeypots to understand threat actor activities and observe trends. This information is used to enhance our security awareness and the services we deliver to our customers.
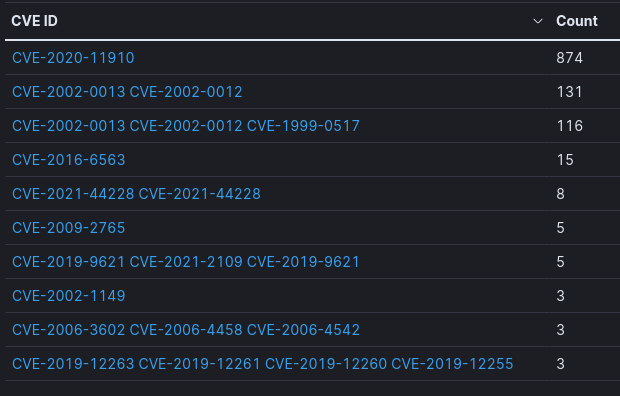
Suricata Top 10 CVEs
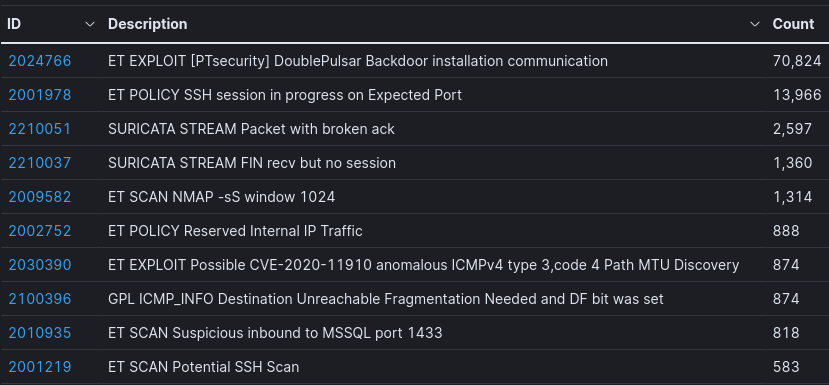
Suricata Top 10 IDS Signatures
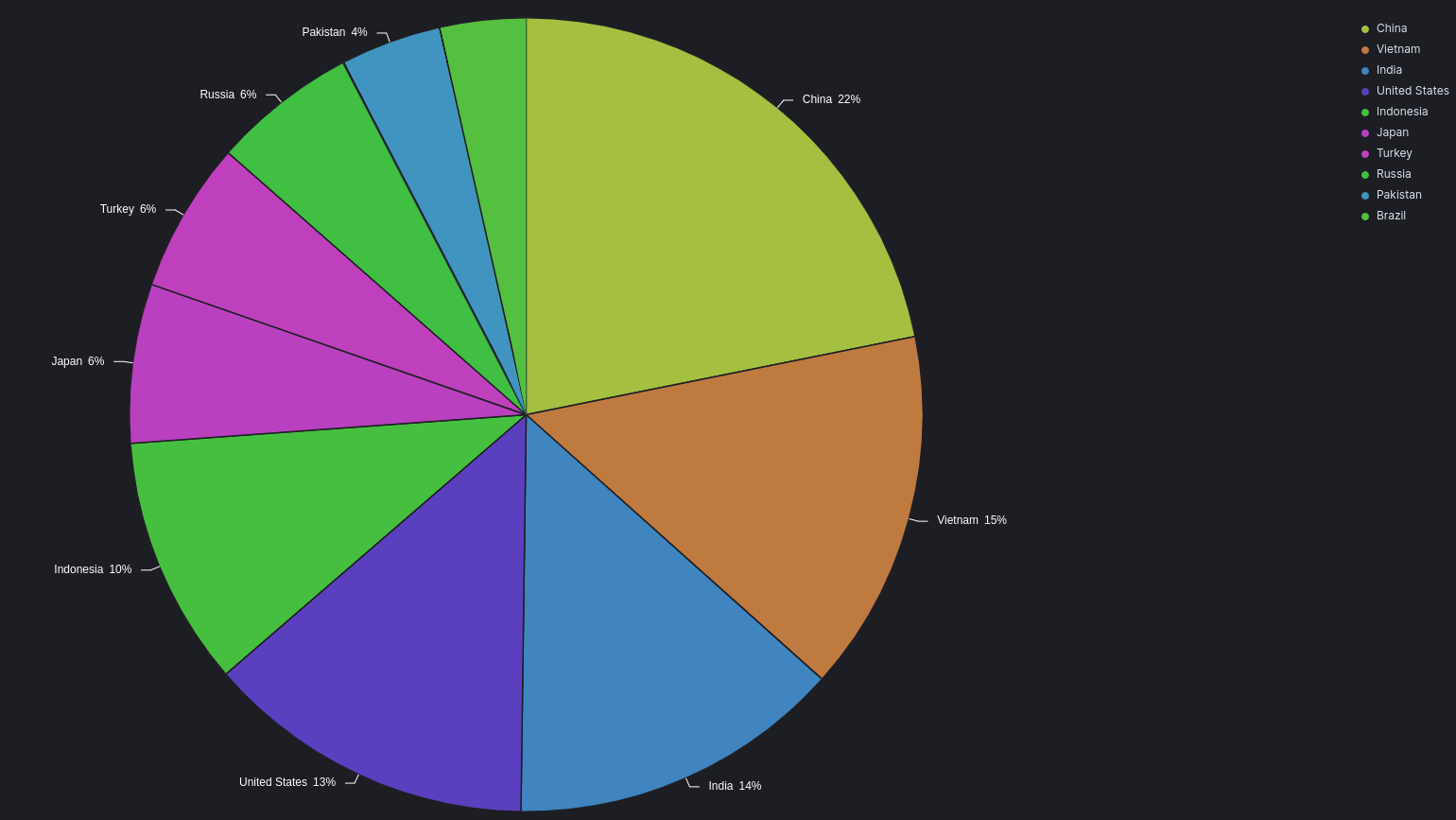
Top Attacks by Source Country
Suricata Top IDS Alert Categories
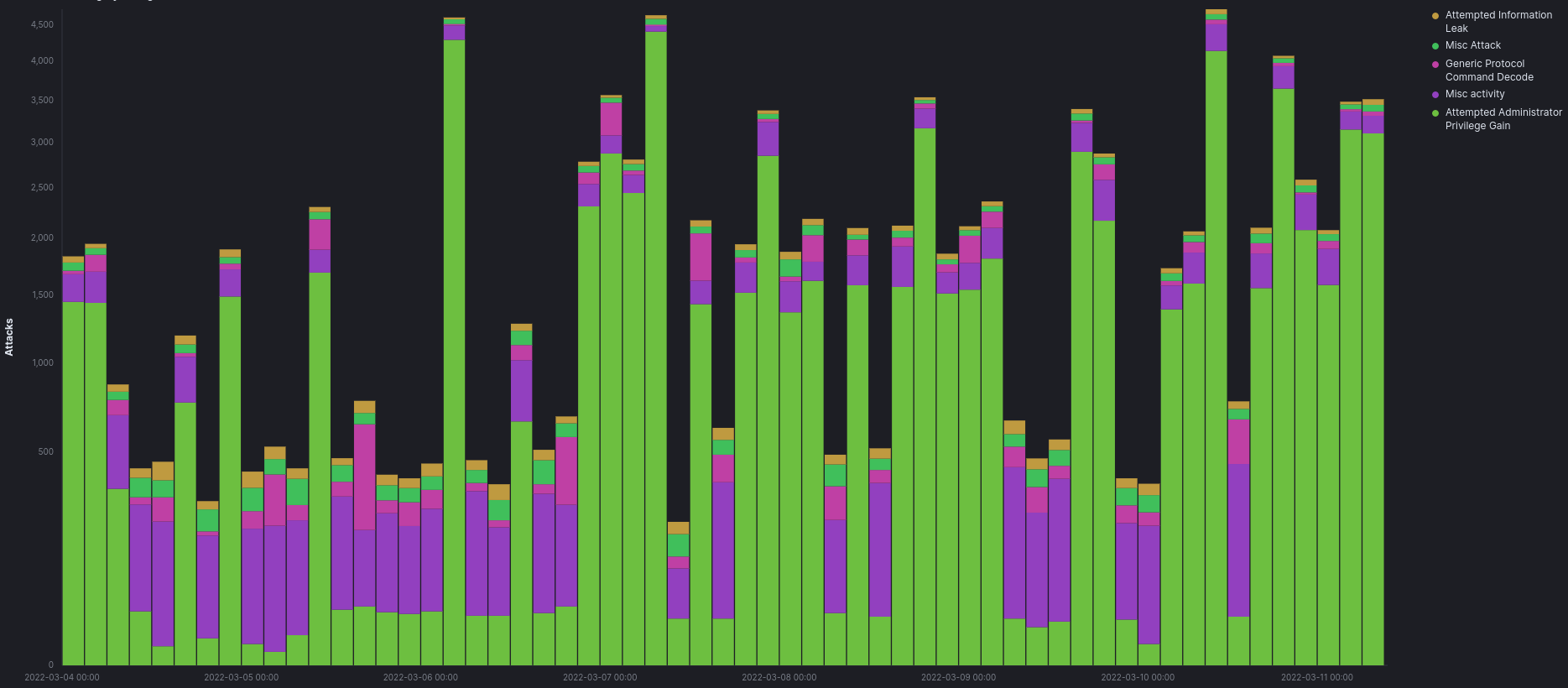
Top Attacks by Destination Port
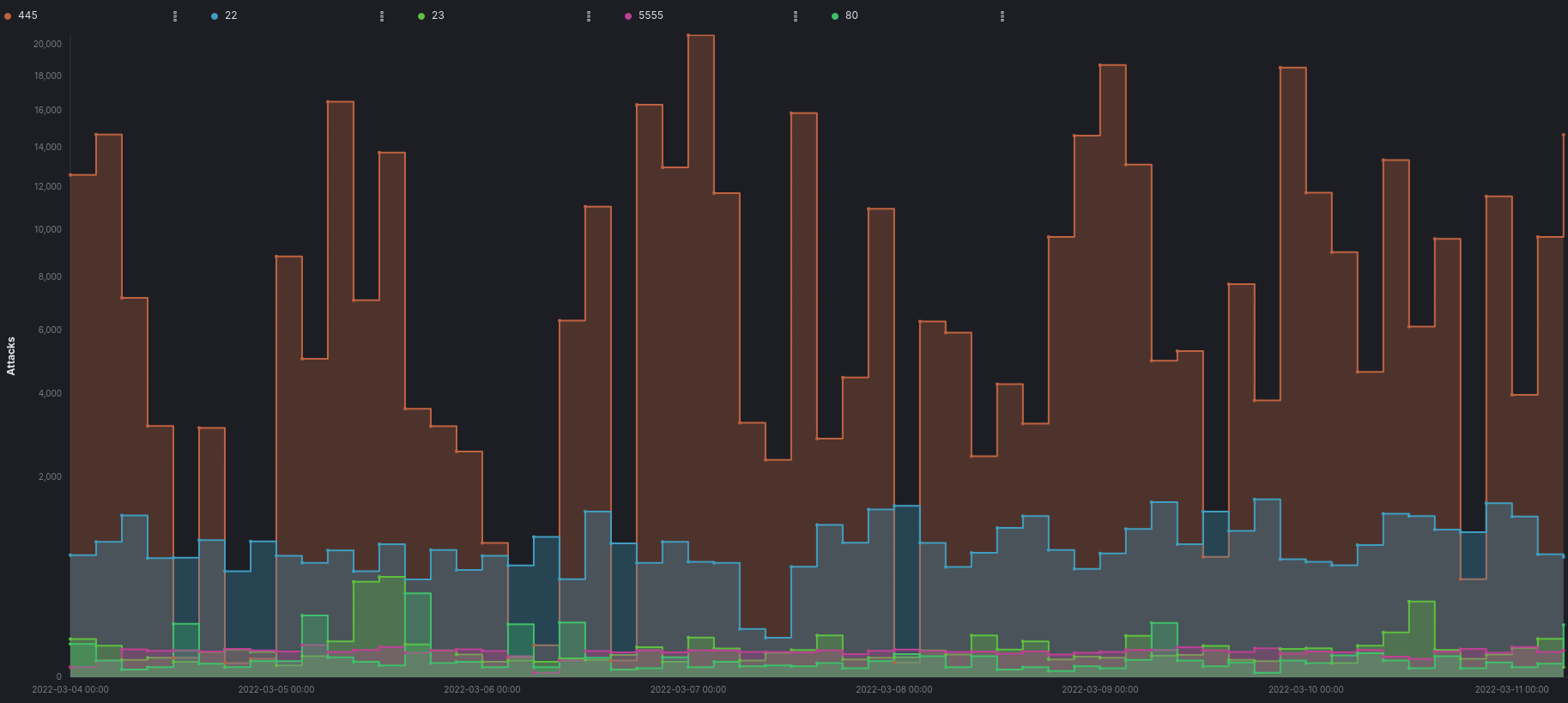
Top Usernames Attempted
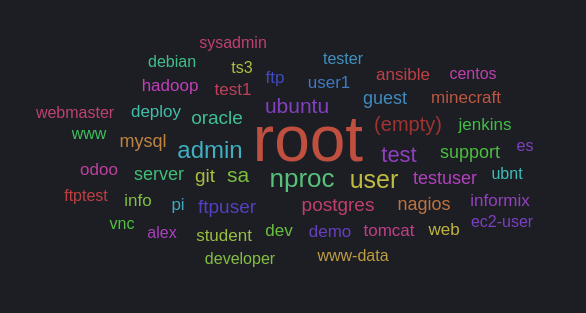
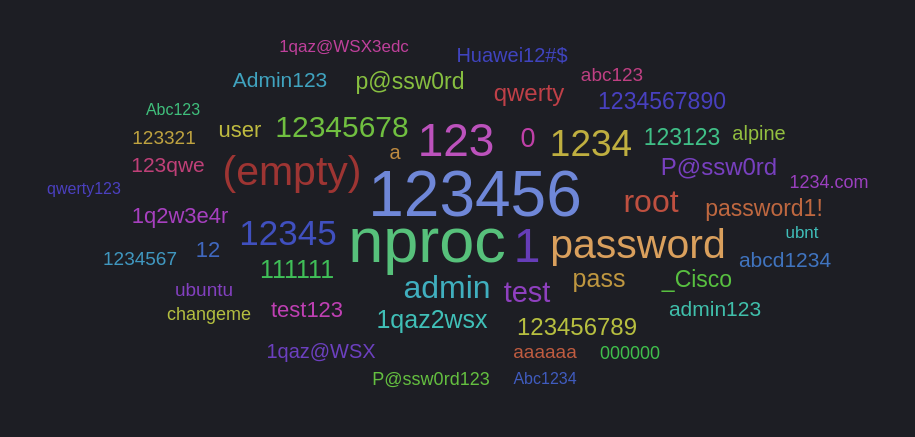
Top Passwords Attempted