Issue Overview
Lots of news has been made recently about an issue in Zoom which reportedly opens users up to attacks whereby a remote threat actor collects the username and the hashed password of the victim. The attacker would then use password cracking tools to decrypt the victim’s password and gain unauthorized access to resources.
The truth is that the underlying issue is with the way Microsoft Windows systems are setup to send the username and hashed password whenever a connection is made to a Windows share, and the attacks are enabled by bad firewall policies and users who click on links without making sure they are legitimate and safe beforehand.
Leaking of Windows password hashes is not new, reports of it go back to at least March, 1997. The problem is caused by a design flaw in Windows whereby If a server requests for the user to authenticate, Windows will try to do so using the user’s credentials which are sent in the form of a clear-text username and a hash of the password which is negotiated between the client and server. The downside to this “user convenience feature” is that any server can request authentication and Windows will happily comply.
Vendor Update
We tested this out in our lab and can verify that this “issue” is fixed in Zoom version 4.6.9 (19253.0401).
Issue Recap
Reviewing this a bit more and discussing it internally, the fact that Zoom renders UNC paths as clickable links isn’t a vulnerability, and may have been by design. For example, if we were in an office setting and wanted to share a link to a document stored on a Windows file server to our team on a Zoom call, sending a UNC path is legitimate. Nothing malicious or wrong in that behavior.
Vectors & Countermeasures
- Practice safe computing and make sure you know where URL links are going to take you before you click on them. Web links start with “http” and Windows share links start with two backslashes, like this “\\server\share”.
- Disable Windows NTLM responses to remote servers via Group Policy in corporate settings, via Local Security Policy for Windows Professional, and via the Registry for Home versions of Windows
- Make sure you have egress filtering enabled and properly configured on your firewalls
There are a few security problems here that need to be addressed which have nothing to do with Zoom, so here they are.
Issue #1 – Unsafe User Habits
Zoom users need to practice good security habits and be sure they understand where a link is taking them before they click it. Having good security awareness really is a HUGE mitigation factor for a lot of attacks.
Issue #2 – Insecure Firewall Configuration
Most tech savvy people understand that a firewall should block unwanted inbound traffic but we run across many who don’t pay attention to the equally important duty which is to restrict outgoing traffic.
Network and Host firewalls should be configured to restrict outbound traffic such that only that which is needed for legitimate purposes is allowed – everything else is denied. Since Windows sends the username and hashed password by default when connecting to a Windows server share, this attack could be mitigated by denying outbound access on Windows SMB and NetBIOS ports at the firewall.
Issue #3 – Insecure Windows Settings
Windows can be configured to stop sending the username and hashed password by modifying the Local Security Policy for individual computers, or by making this change effective across lots of computers in a Domain by using Group Policy Objects.
Figure 1 – Deny sending NTLM credentials to remote servers using Windows policies
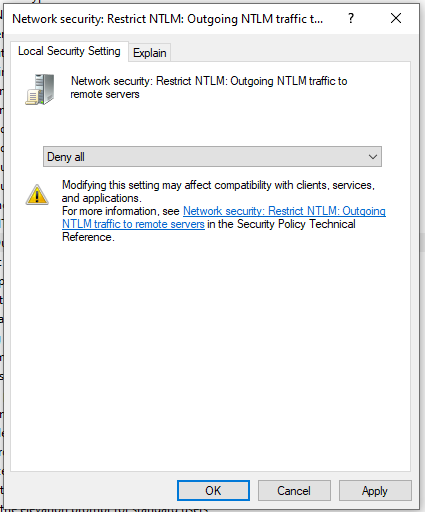
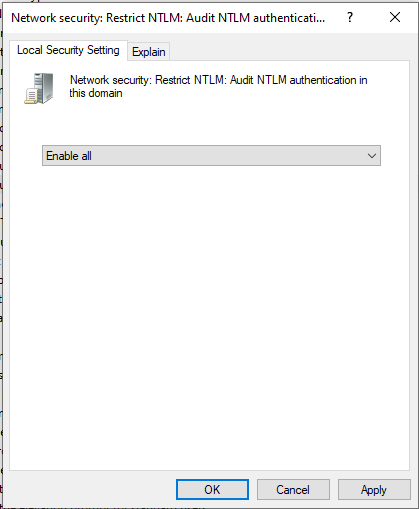
Figure 2 – Enable NTLM Auditing
Conclusion
Good security practices go a long way to preventing security breaches and the responsibility falls not only on business end-users, but on security architects, engineers, and administrators of IT environments in conjunction with the management team, who should be driving the risk prevention program for the organization and enabling a strong cybersecurity posture. Operating systems, software, cloud providers, and business applications are going to have vulnerabilities so we need to prepare in advance by implementing a security program that covers prevention, detection, response and recovery.

