Data Breaches & Cyber Attacks
LAPSUS$ Cyber-Attacks
LAPSUS$ is a relatively new threat actor group who is responsible for cyber-attacks on OKTA and Microsoft, as announced this month. LAPSUS$ is also tied to cyber-attacks against NVIDIA, Samsung, and Vodafone, where the group posted screenshots showing evidence of those successful attacks.
A key bit of information provided by the LAPSUS$ attacker group regarding the OKTA breach is that they are looking for credentials and access for MSPs and MSSPs that use OKTA. This is no doubt so that they can have inroads into those organizations, and compromise their clients.
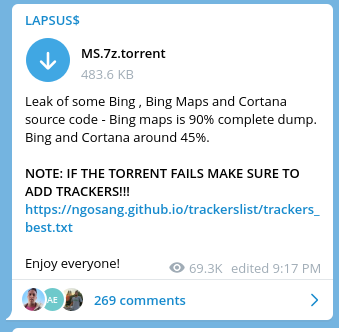
LAPSUS$ has screenshots showing evidence of their successful attack on Microsoft, and as their Telegram post shows, they have access to Microsoft source code for Bing and Cortana.
It appears that LAPSUS$ makes heavy use of social engineering attacks such as phishing to compromise credentials and gain access to target organizations.
Microsoft said LAPSUS$ has been known to target the personal email accounts of employees at organizations they wish to hack, knowing that most employees these days use some sort of VPN to remotely access their employer’s network.
Possible Arrest of LAPSUS$ leader: A 16-year-old from Oxford has been accused of being one of the leaders of cyber-crime gang Lapsus$.
The BBC is reporting the arrest of a 16-year-old from Oxford, who amassed a $14m fortune through hacking.
https://www.bbc.com/news/technology-60864283
Recent Threat Highlights
| Critical | CVE-2022-2295- Carbon Black App Control- The flaw exists because user input isn’t properly validated. An attacker looking to exploit the bug needs to be authenticated as a high-privileged user and requires network access to the App Control interface in order to execute commands on the server. https://www.securityweek.com/vmware-patches-critical-vulnerabilities-carbon-black-app-control | |||
| High | Dell Bios Vulnerabilities- CVE-2022-24415, CVE-2022-24416, CVE-2022-24419, CVE-2022-24420, and CVE-2022-24421- Dell BIOS contains an improper input validation vulnerability. A local authenticated malicious user may potentially exploit this vulnerability by using an SMI to gain arbitrary code execution during SMM.
https://thehackernews.com/2022/03/new-dell-bios-bugs-affect-millions-of.html |
|||
Cyber Intel by Industry
| Cyber / MSP / MSSP | Lapsus$ hacked Okta this week. They also claim to have had “Superuser/Admin” access to Okta’s systems for two months, and said its focus was “only on Okta customers.”
https://cybersecop.com/news/2022/3/22/advisory-reports-of-possible-digital-breach |
|||
| Healthcare | East Tennessee Children's Hospital fell victim to an "information technology security issue" on March 13, according to a notice on its website. On March 14, the hospital told patients via Facebook that X-Ray services would not be available at any Children's Hospital Urgent Care Centers for the remainder of the night. By March 22, the hospital informed patients that the phones in all its external offices were fully operational again. "Our cyber forensics teams and outside agencies are doing everything possible to minimize any disruption. The response is active and still ongoing," the notice on ETCH's website stated. "We apologize for any inconvenience, and ask for your patience as we address this issue." https://healthitsecurity.com/news/kentucky-tennessee-hospitals-begin-cybersecurity-incident-recovery | |||
| SaaS Providers | Lapsus$, a cyber extortion gang, has announced that they have breached Microsoft. The gang has leaked torrents containing source code for Bing, Bing Maps, and Microsoft Cortana, as well as a screenshot of an internal Microsoft Azure DevOps account.
https://cybersecop.com/news/2022/3/22/advisory-reports-of-possible-digital-breach |
|||
| Financial Services | A hacking group tracked as UNC2891 is using a new Unix rootkit named Caketap to intercept banking card and PIN verification data from compromised ATM switch servers and carry out unauthorized transactions. https://cyware.com/news/caketap-rootkit-by-unc2891-targets-banks-customers-73c5bdf8 |
|||
| Biotech / Pharma | Hospitals and medical device companies are on heightened alert for cyber-attacks from Russian-sponsored hackers looking to target U.S. critical infrastructure after Russia's invasion of Ukraine
https://www.medtechdive.com/news/medtech-hospitals-alert-cyberattacks-russia-ukraine/619486/ |
|||
| Government | FBI and Cybersecurity and Infrastructure Security Agency have issued a new joint advisory warning American and allied satellite owners and operators that they “are aware of possible threats to U.S. and international satellite communication networks.” https://www.scmagazine.com/analysis/apt/agencies-aware-of-hacking-threats-to-us-allied-satellite-networks | |||

