Recent Threat Highlights
| Critical | A update was released earlier this week for google chrome to address the previously mentioned critical and high vulnerabilities. Current version is 99.
CVE-2022-24086- Adobe Commerce versions 2.4.3-p1 (and earlier) and 2.3.7-p2 (and earlier) are affected by an improper input validation vulnerability during the checkout process. Exploitation of this issue does not require user interaction and could result in arbitrary code execution. |
|||
| High | CVE-2021-32586- An improper input validation vulnerability in the web server CGI facilities of FortiMail before 7.0.1 may allow an unauthenticated attacker to alter the environment of the underlying script interpreter via specifically crafted HTTP requests. FortiNet has posted possible solutions at the site listed below.
https://www.fortiguard.com/psirt/FG-IR-21-008 CVE-2022-24718- ssr-pages is an HTML page builder for the purpose of server-side rendering (SSR). In versions prior to 0.1.4, a path traversal issue can occur when providing untrusted input to the `svg` property as an argument to the `build(MessagePageOptions)` function. While there is no known workaround at this time, there is a patch in version 0.1.4. |
|||
Cyber Intel by Industry
| Cyber / MSP / MSSP | Acronis SCS – an American cyber protection company dedicated to providing certified solutions to the US public sector, announced today the launch of Acronis SCS Cyber Protect Cloud, a first of its kind approach for cyber protection, ranging from backup to security. Acronis SCS Cyber Protect Cloud is designed to help drive Managed Service Providers (MSPs) operational efficiency while protecting our nation's networks. | |||
| Healthcare | This week, two Illinois healthcare organizations began notifying patients of separate healthcare data breaches that caused protected health information (PHI) exposure. South Shore Hospital in Chicago faced an unspecified hacking incident, and Harvey, Illinois-based Family Christian Health Center informed patients of a ransomware attack. Collectively, the two incidents impacted nearly 200,000 individuals. SSH discovered suspicious network activity on December 10, 2021. The hospital immediately activated its emergency protocols and engaged with a third-party forensics firm. It is unclear whether threat actors exfiltrated files or if ransomware was involved. The impacted files contained names, birth dates, Social Security numbers, health insurance information, diagnoses, Medicare and Medicaid information, financial information, and addresses. |
|||
| SaaS Providers | Over the past year SaaS applications have vastly increased the attack surface; they’re ripe for exploitation due to mass adoption across many organizations. This enables attackers to concentrate their efforts on a handful of SaaS providers to simultaneously impact large numbers of their customers. For instance, in July a ransomware attack paralyzed 1,500 organizations by compromising SaaS-based software from Kaseya, which is used for remote IT management. Experts agree that the Kaseya hack set off a race among criminals searching for similar vulnerabilities.
https://threatpost.com/supply-chain-pain-and-changing-security-roles/177058/ |
|||
| Financial Services | Russia appears to have officially declared cyber war on the United States.
Bank executives have spent billions of dollars in recent years to protect against cyber criminals but they say the recent wave of attacks is different. Sources describe them as a subtle but intensified assault in banks' technological infrastructure. https://nypost.com/2022/03/01/russian-cyber-attacks-against-us-banks-increasing/ |
|||
| Biotech / Pharma | Constella recently released a pharma oriented cybersecurity report. In the 20 companies Constella analyzed they found that 5 clocked more than 200,000 total data exposures and breaches, with some climbing as high as 400,000. These pharma vulnerabilities crop up when third-party domains are breached. This often leads to personal data like names, passwords and phone numbers turning up for sale on the deep and dark webs.
What Constella is seeing, essentially, is that many employees and executives are using company credentials to log into third-party websites. “When we see corporate credentials being used on nonessential sites—gaming sites, adult sites, social media sites—it’s an indicator that employees are incurring serious cyber risk,” Nelson explained. |
|||
| Government | US government entities are preparing for a full scale cyber attack from Russia in retaliation for the sanctions placed. There are two types of cyberattacks: ones that have an indirect impact on people's livelihood and attacks targeting the tech of specific people. Javed Ali, the former senior director of counterterrorism at the National Security Council said it's hard to predict if Russia would take such action on the West since it would cause an immediate retaliation from countries with their own state of the art tools and tactics however it is likely to happen. The Department of Homeland Security, the agency tasked with the domestic response to the invasion in Ukraine, has set up a page on the Cybersecurity and Infrastructure Security Agency’s website specifically warning of cyber-attacks emanating from Russia. While the FBI has also notified everyone to report any and all cyber attacks originating from Russia to them via the various reporting methods. https://abcnews.go.com/International/shields-cyberattack-affect-americans-prepare/story?id=83085211 |
|||
Weekly Honeypot Stats for March 4, 2022
The following are curated from our network of honeypots which are exposed to Internet traffic. Legion Cyberworks uses our network of honeypots to understand threat actor activities and observe trends. This information is used to enhance our security awareness and the services we deliver to our customers.
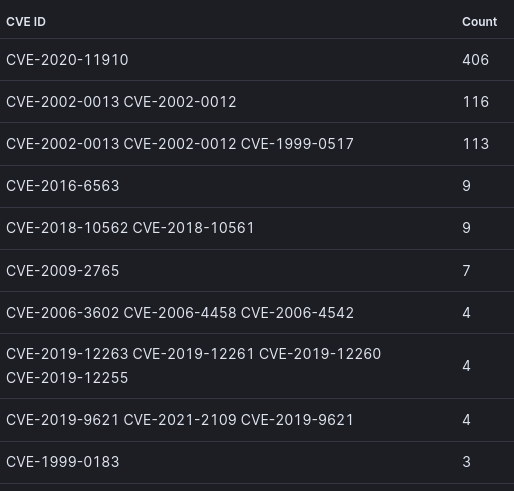
Suricata Top 10 CVEs
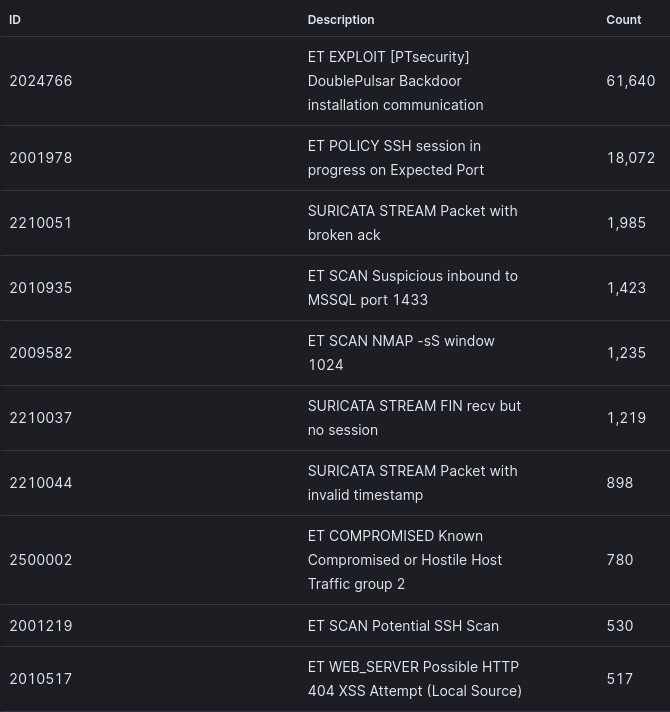
Suricata Top 10 IDS Signatures
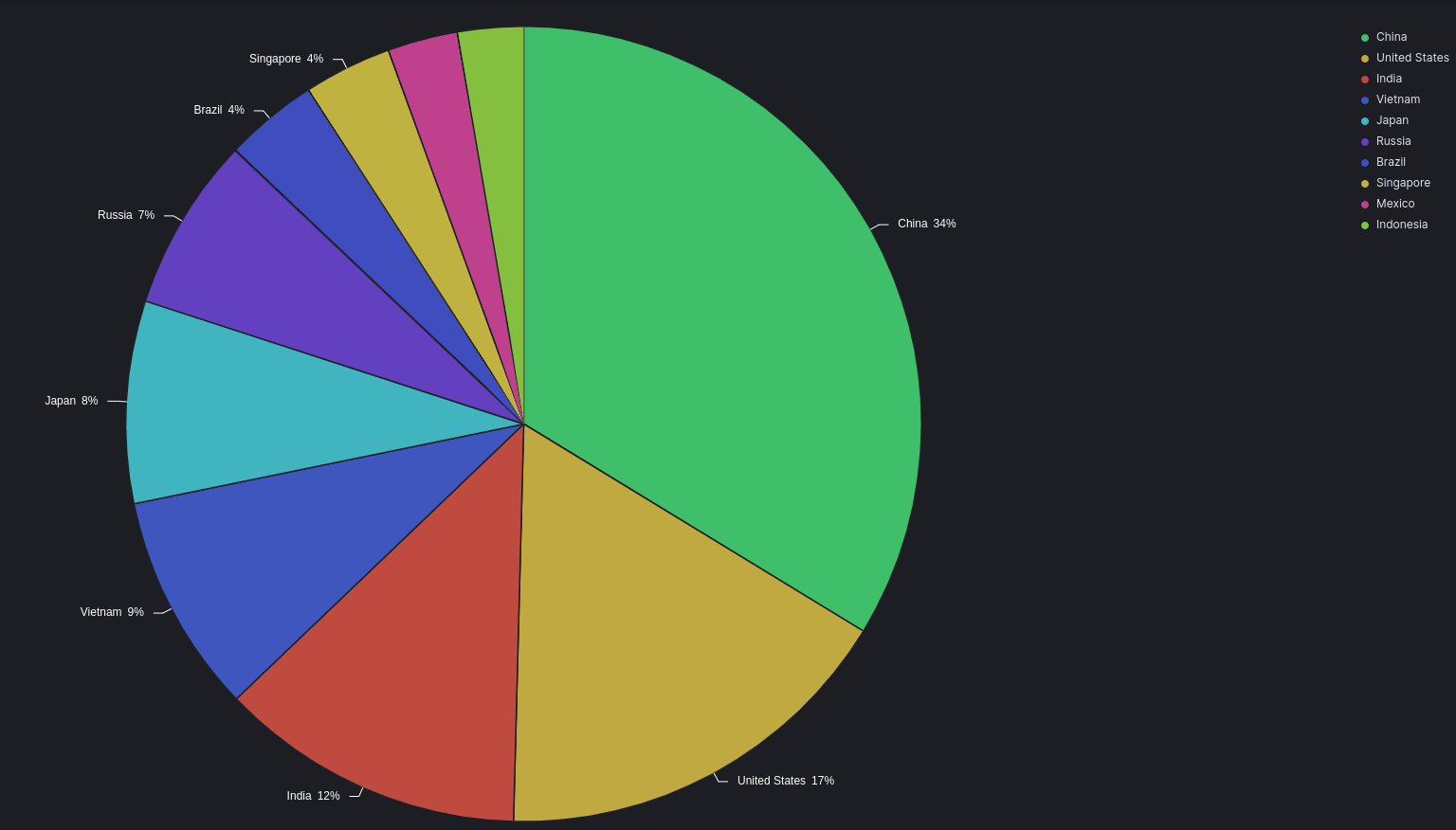
Top Attacks by Source Country
Suricata Top IDS Alert Categories

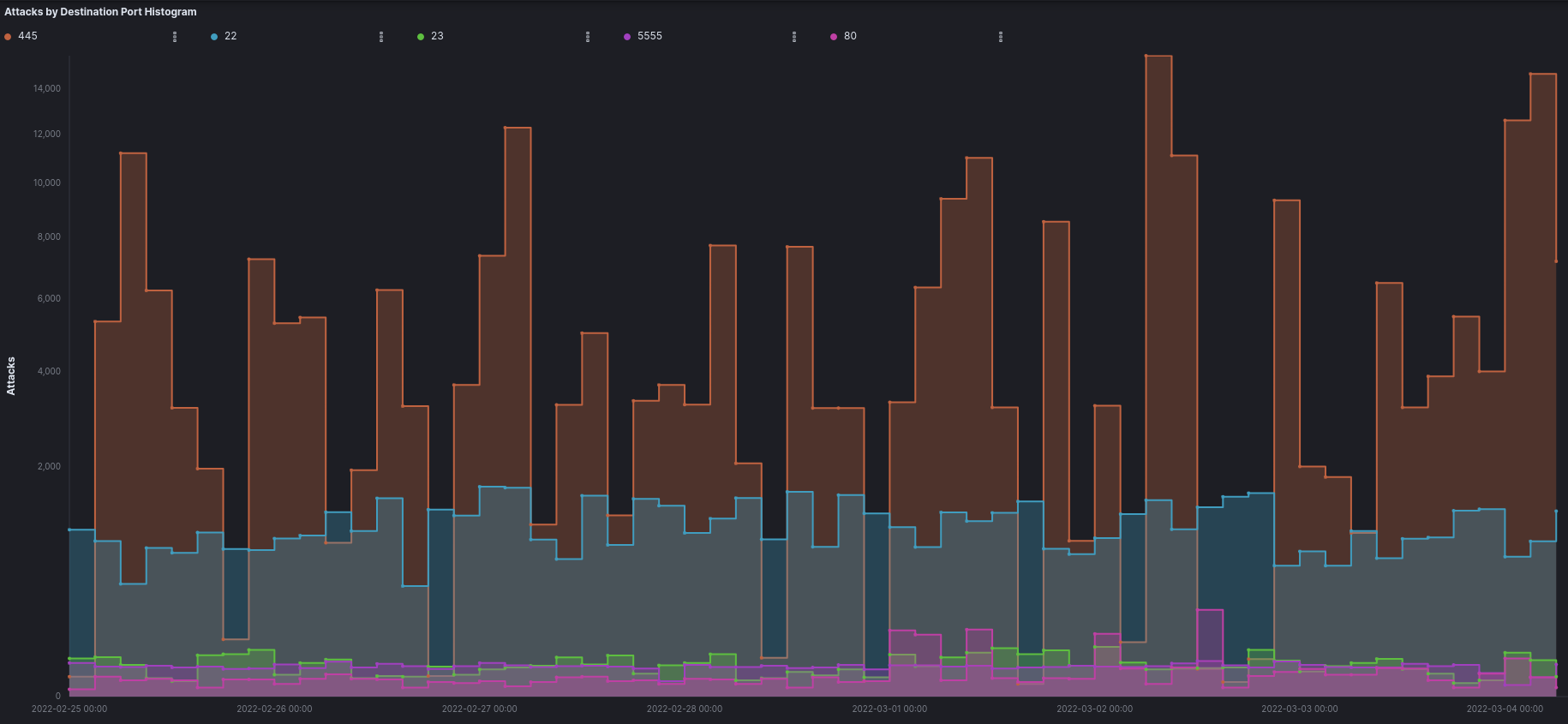
Top Attacks by Destination Port
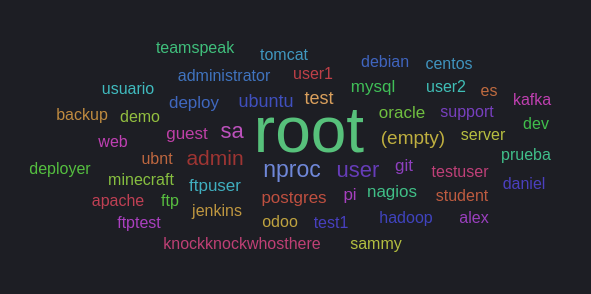
Top Usernames Attempted
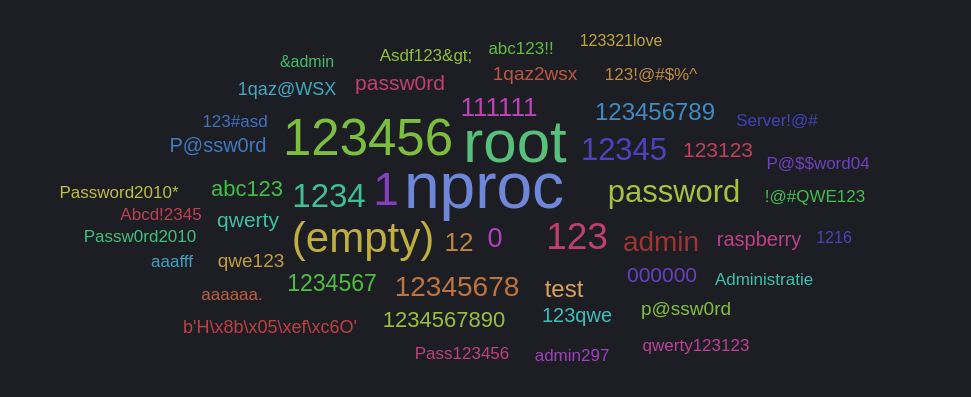
Top Passwords Attempted