Introduction
In the realm of cybersecurity, the battle against advanced persistent threats (APTs) has intensified. Among the notable adversaries is the Volt Typhoon APT group, a state-sponsored threat actor based out of China, known for their sophisticated and targeted attacks and their focus on espionage and information gathering activities.
In this blog post, we will delve into the tactics, techniques, and procedures (TTPs) employed by Volt Typhoon, and explore how Legion's solutions can help organizations mitigate these risks effectively.
Understanding the Volt Typhoon APT Group
The Volt Typhoon APT group has emerged as a formidable cybersecurity adversary, employing sophisticated tactics to target high-value organizations. Their activities pose significant business, legal, and financial risks.
Volt Typhoon has been active since mid-2021 and has targeted critical infrastructure organizations in Guam and elsewhere in the United States. Based on observed behavior, the threat actor likely intends to conduct espionage and maintain long-term persistence within compromised environments.
Like many other advanced threat groups, Volt Typhoon employs a technique called "Living off the Land" (LotL) to evade detection and carry out its malicious activities. LotL refers to the practice of utilizing legitimate tools, utilities, and protocols already present on a target system to carry out malicious actions, rather than relying on custom or malicious software.
Examples of LotL include:
Exploiting legitimate administrative tools: Volt Typhoon leverages common system administration tools, such as PowerShell, WMI (Windows Management Instrumentation), or command-line utilities like PsExec and Netsh, to execute commands and carry out various malicious activities. These tools are often present on Windows-based systems and are used by system administrators for legitimate purposes, making it difficult for security solutions to differentiate between normal and malicious activities.
Abusing trusted applications: The threat actors take advantage of trusted applications already installed on target systems. By exploiting vulnerabilities or misconfigurations in applications like Microsoft Office, web browsers, or PDF readers, they can execute malicious code or deliver malware without raising suspicion.
Fileless malware and memory-resident attacks: Volt Typhoon frequently employs fileless malware techniques that reside solely in memory and do not leave traces on the victim's disk. This approach helps them evade traditional antivirus solutions that rely on file scanning. Memory-resident attacks involve leveraging scripting languages like PowerShell or VBScript to execute malicious code directly in memory, bypassing traditional security measures.
Network protocol abuse: The APT group abuses legitimate network protocols, such as HTTP, DNS, or FTP, to establish command and control (C2) channels or exfiltrate stolen data. By blending their malicious traffic with normal network traffic, they aim to avoid detection by network security systems.
Credential theft and privilege escalation: Volt Typhoon focuses on gaining unauthorized access to systems and networks by stealing credentials through techniques like phishing, spear-phishing, or credential harvesting. Once inside the target environment, they employ privilege escalation techniques, such as exploiting vulnerabilities or misconfigurations, to gain higher levels of access and move laterally across the network.
Sandbox evasion: To avoid detection in sandboxes and security analysis environments, Volt Typhoon utilizes LotL techniques to make their malicious activities appear benign or similar to legitimate user actions. By mimicking user behavior and leveraging trusted tools, they can bypass sandbox-based security defenses.
These Living off the Land tactics allow Volt Typhoon APT to remain stealthy, evade detection, and prolong their presence within targeted networks. Organizations combating such advanced threats must employ comprehensive security measures, including behavioral analysis, anomaly detection, and monitoring of system activity and network traffic to identify and mitigate such attacks effectively.
Business Risks Posed by Volt Typhoon
Data Breaches and Loss of Intellectual Property: A successful breach can result in the theft of sensitive data, including intellectual property and customer information. Such data breaches can severely damage an organization's reputation and competitiveness, leading to financial losses and loss of trust.
Operational Disruption: Infiltration of an organization’s infrastructure can lead to significant operational disruptions, including system downtime, loss of productivity, and compromised business continuity. These disruptions can have far-reaching consequences, affecting critical business processes and leading to financial losses.
Legal and Compliance Issues: Falling victim to cyber-attacks can expose organizations to legal and compliance challenges. Compliance regulations, such as data protection and privacy laws, may require organizations to notify affected individuals and authorities, potentially resulting in legal liabilities and financial penalties.
Reputational Damage: A successful attack can tarnish an organization's reputation, eroding customer trust and loyalty. Negative publicity and the perception of inadequate cybersecurity measures can have long-lasting effects on an organization's brand value and customer relationships.
Common TTPs of Volt Typhoon
Spear Phishing: Volt Typhoon leverages tailored spear phishing campaigns to deceive employees into disclosing sensitive information or executing malicious code. These emails often appear legitimate, exploiting trust and familiarity to gain unauthorized access to corporate systems where the adversary can steal sensitive information, deploy ransomware, and establish persistence to conduct further attacks.
Watering Hole Attacks: The Volt Typhoon APT group compromises trusted websites frequented by target individuals or organizations. By injecting malicious code into these sites, they exploit vulnerabilities in visitors' browsers, allowing them to gain unauthorized access to sensitive information.
Zero-day Exploits: Like many prolific APT groups, Volt Typhoon actively searches for undisclosed software vulnerabilities, known as zero-day exploits, to bypass security measures. By utilizing these vulnerabilities before they are patched, they can gain unauthorized access to systems and maintain long-term persistence.
Backdoor Implants: Once inside a targeted network, Volt Typhoon deploys stealthy backdoor implants to maintain persistent access. These implants allow them to return undetected and exfiltrate sensitive information over an extended period, prolonging the impact of their attacks.
Mitigating Risks with Solutions from Legion Cyberworks
Legion Cyberworks offers a comprehensive suite of solutions that are specifically designed to detect and prevent APT attacks like those executed by the Volt Typhoon APT group and other threat actors. With state-of-the-art tooling that leverages machine learning, artificial intelligence, algorithm driven response actions, and behavioral analysis techniques, our solutions can identify and neutralize suspicious activities within the network.
By employing proactive security measures, organizations can fortify their defenses and safeguard critical assets from potential breaches. This is precisely what you get with solutions from Legion Cyberworks.
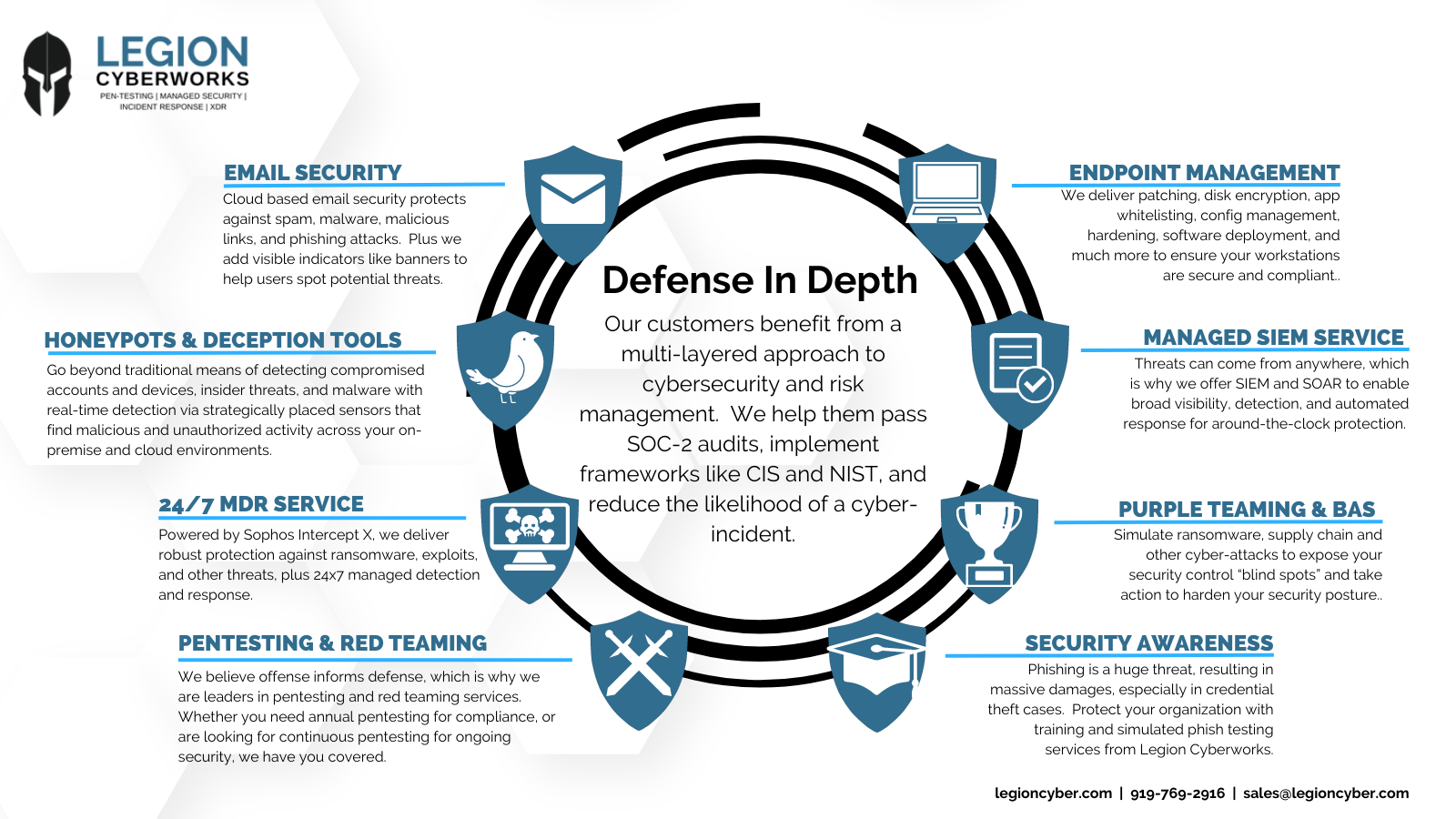
Email Security Filtering and Threat Prevention: Email and compromised accounts are one of the primary means APTs and other threat actors infiltrate organizations. This is often accomplished through phishing for credentials and/or access, delivering malware and malicious URLs via email, and through using stolen credentials to simply login as a valid user within your environment. Legion partners with Sophos and OnDefend to deliver powerful layered email security that protects your organization and workforce against email based attacks like phishing, malware, and malicious links.
Advanced Threat Detection and 24x7 Managed Response Services: Legion's solutions provide advanced threat detection capabilities, leveraging artificial intelligence and machine learning algorithms, combined with a fully staffed SOC to deliver 24x7 response services that limit the scope and damage of an attack. By rapidly identifying and responding to potential threats, Legion can minimize the impact of attacks and swiftly mitigate risks. Our 24x7 MDR Service can be deployed using your existing EDR solution including Sophos, Crowdstrike, Microsoft Defender, SentinelOne, and others.
Comprehensive Security and Risk Assessments: Legion offers comprehensive security and risk assessments to identify missing processes, gaps in your controls (SOC-2, ISO, HITRUST, and more) as well as system and architecture weaknesses. We provide actionable recommendations you can use to improve your security posture. By proactively addressing weak points, organizations can fortify their defenses and reduce the likelihood of successful attacks, while also achieving and maintaining their required level of compliance needed to operate as a business.
Purple Teaming Exercises: Simulate ransomware, attacker TTPs and other threats within your server and workstation environments to uncover and correct blind spots in your tooling, processes, and other security controls. Access detailed dashboards, drill-down into the data, and empower your security team to take action to harden your security posture and optimize prevention, detection, and response capabilities. Work directly with our team throughout the engagement for an expert led experience that will absolutely improve your security posture. If you are using an MSSP / SOC provider, this is an excellent way to team up with them to measure adherence to SLAs and improve their services for your business.
Proactive Security via Red Teaming Services: We provide our clients with red teaming and penetration testing services that pinpoint weaknesses and gaps in systems, applications, networks, and security controls. We work collaboratively with our clients to prioritize remediation efforts to focus on what matters most - exploitable weaknesses that are going to get you hacked. Legion offers a variety of offensive security services to cover your infrastructure, cloud, web applications, and more.
Distributed Deception & Honeypot Infrastructure: Adversaries like Volt Typhoon and others use compromised credentials and assets within your network to pivot and move laterally, often looking for sensitive information & data, databases, and additional credentials they can use to further embed themselves into your enterprise. Our distributed deception tools give you an edge, providing near real time notification of suspicious activity within your network so that you can quickly take action to isolate and contain threats, thereby reducing your overall risks.
Scalable and Adaptive Security Solutions
Legion Cyberworks understands that cybersecurity requirements vary across organizations of different sizes and industries. Our solutions are scalable and adaptable to meet the unique needs of each client.
Whether you are a small business or a large enterprise, Legion's solutions integrate into existing network infrastructures and the tools, applications, and platforms you are already using, providing a customized and comprehensive security framework.
Legion's Commitment to Excellence
Legion Cyberworks has established itself as a trusted partner in the cybersecurity industry, with a proven track record of delivering innovative solutions to customers across a diverse array of industries.
Our absolute focus on protecting our clients, continuous improvement, the use of cutting edge technologies and constant refinement of our processes, ensures that our offerings remain at the forefront, empowering organizations to stay one step ahead of APT threats.
With Legion's solutions, organizations can rest assured that their business is fortified against sophisticated adversaries like the Volt Typhoon APT group and others who seek to cause you harm.
Conclusion
Volt Typhoon and other APTs represent a formidable cybersecurity challenge, but with the right tools and strategies in place, organizations can effectively defend against such threats.
Solutions from Legion Cyberworks provide a robust prevention and defense framework, enabling proactive discovery and remediation of weaknesses, 24/7 threat detection and response, network visibility, delivered with scalability and a options for additional security solutions that can be plugged in to meet your current and future needs.
By partnering with Legion Cyberworks, organizations can bolster their security posture and safeguard their digital assets in the face of evolving attacks.
Contact Us
We’re ready to work together with your organization to build a sustainable security model that will change and scale right along with your organization. You can reach us online at https://legioncyber.com/contact by phone at 919-769-2916, or via email at [email protected]. We’re looking forward to working with you!