Recent Threat Highlights
| Critical | CVE-2022-24086- Critical Magento 0-Day Vulnerability- Improper input validation issue that could be weaponized to achieve arbitrary code execution. It's a pre-auth flaw, which means it could be exploited without requiring credentials.
https://thehackernews.com/2022/02/critical-magento-0-day-vulnerability.html |
|||
| High | Multiple vulnerabilities in Google Chrome browser
CVE-2022-0603- Use after free in File Manager. These vulnerabilities/bugs affect Stable Channel and Extended stable channel. Google released security updates this week to address these issues. https://chromereleases.googleblog.com/2022/02/stable-channel-update-for-desktop_14.html |
|||
Recent Threats by Industry
| Cyber / MSP / MSSP | This week SonicWall released their 2022 Cyber Threat Report. In this report they summarized the past year of cyber activity and threat trends. SonicWall's Real-Time Deep Memory Inspection technology discovered 65% more "never before seen" malware variants than the year before. This stresses the importance that MSP's stay up to date on the latest cyber trends, attack techniques and tools used by threat actors. https://markets.businessinsider.com/news/stocks/sonicwall-threat-intelligence-confirms-alarming-surge-in-ransomware-malicious-cyberattacks-as-threats-double-in-2021-1031204106 | |||
| Healthcare | The recent cyberattack on the International Committee of the Red Cross (ICRC), which compromised the data of more than 515,000 “highly vulnerable” people, was likely the work of state-sponsored hackers. Hackers gained access to the ICRC’s network by exploiting a known but unpatched critical-rated vulnerability in a single sign-on tool developed by Zoho, which makes web-based office services. https://techcrunch.com/2022/02/16/red-cross-links-january-cyberattack-to-state-sponsored-hackers/ | |||
| SaaS Providers | A cyberattack targeting News Corp journalists represents the latest stern reminder that MSSPs and MSPs need to audit and safeguard customers’ cloud and SaaS services. News Corp relies on third-party providers for certain technology and “cloud-based” systems and services that support a variety of business operations.The Company’s preliminary analysis indicates that foreign government involvement may be associated with this activity, and that data was taken. https://www.msspalert.com/cybersecurity-breaches-and-attacks/news-corp-cyberattack-involved-cloud-software-supply-chain/ | |||
| Financial Services | Ukraine accused Russia on Wednesday of being behind a cyber-attack that targeted two banks and its defence ministry, which the country’s deputy prime minister said was the largest of its type ever seen. | |||
| Biotech / Pharma | Morley Companies, a Saginaw, Michigan provider of business services, disclosed it had been hit by ransomware attack on August 1, 2021 that enabled hackers to steal data belonging to current employees, former employees and some clients. Morley suspects that names, addresses, social security numbers, birth dates, client identification numbers, medical diagnostic and treatment information, and health insurance information were pilfered in the cyber heist. | |||
| Government | Hackers backed by the Russian government have breached the networks of multiple US defense contractors in a sustained campaign that has revealed sensitive information about US weapons-development communications infrastructure, the federal government said on Wednesday. The campaign started in January 2020 and has continued through this month according to a joint advisory by the FBI, NSA, and the CISA. | |||
Data Privacy and Security Law
| Regulatory Forecast | If 2021 is any indication of the changes coming to security laws, in 2022 we expect these changes to continue on a larger scale. Below I have posted a recap of changes in 2021. | |||
| Data Privacy and Security Law |
On February 2, 2022, the Massachusetts Legislature’s Joint Committee on Advanced Information Technology, the Internet and Cybersecurity released a new draft of a bill designed to provide mechanisms for how personal information is used and to control how companies use such information. |
|||
Weekly Honeypot Stats for February 18, 2022
The following are curated from our network of honeypots which are exposed to Internet traffic. Legion Cyberworks uses our network of honeypots to understand threat actor activities and observe trends. This information is used to enhance our security awareness and the services we deliver to our customers.
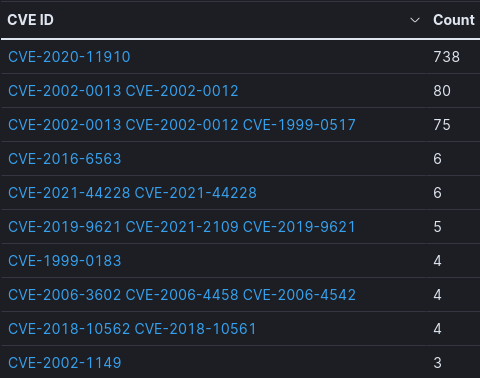
Suricata Top 10 CVEs
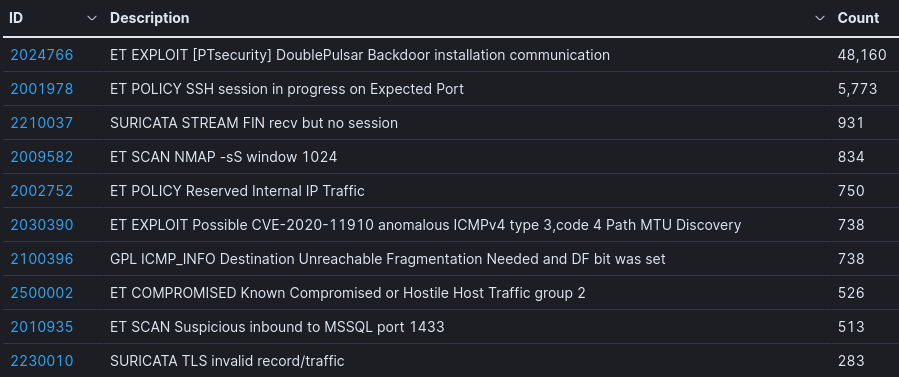
Suricata Top 10 IDS Signatures
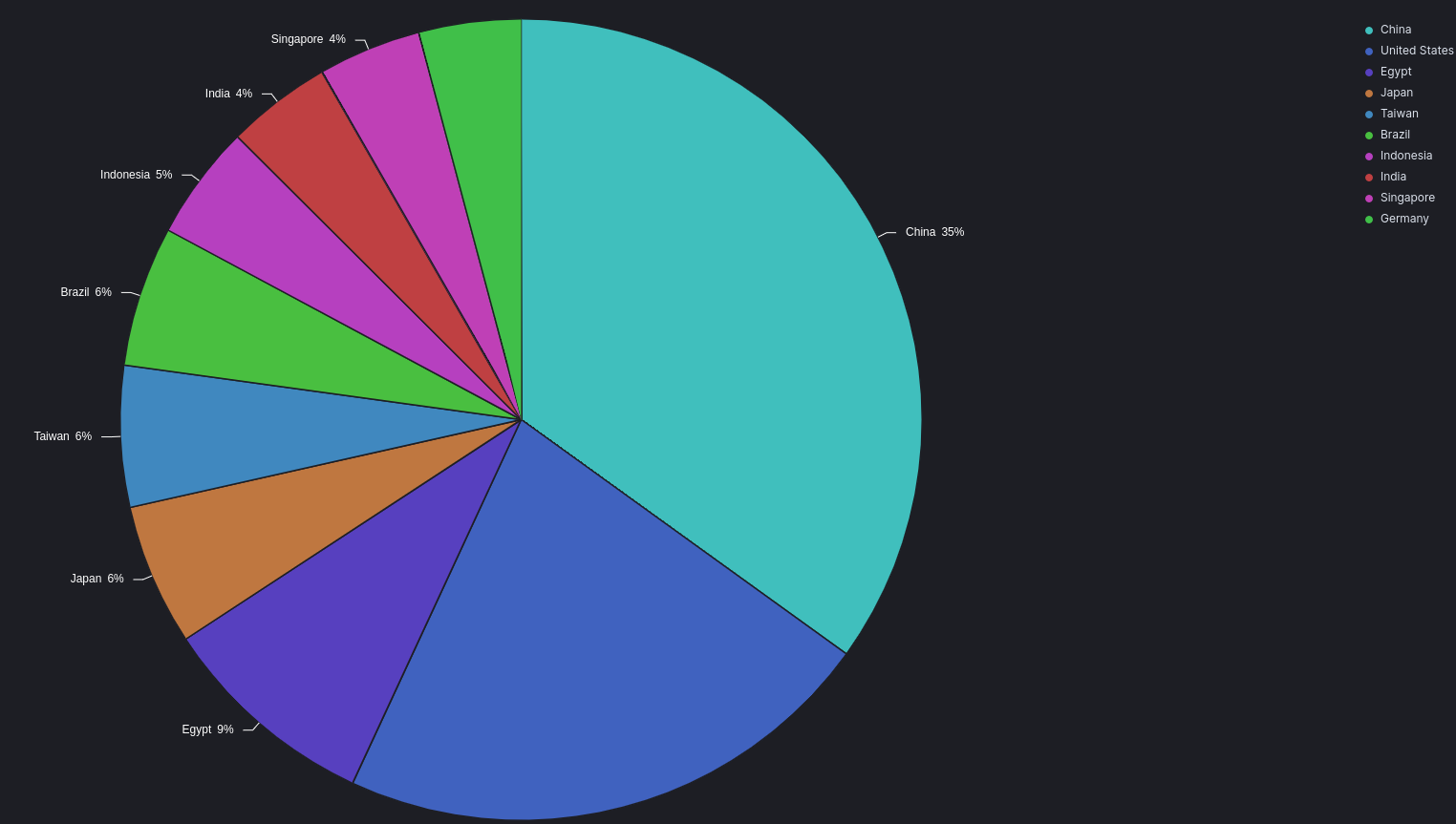
Top Attacks by Source Country
Suricata Top IDS Alert Categories
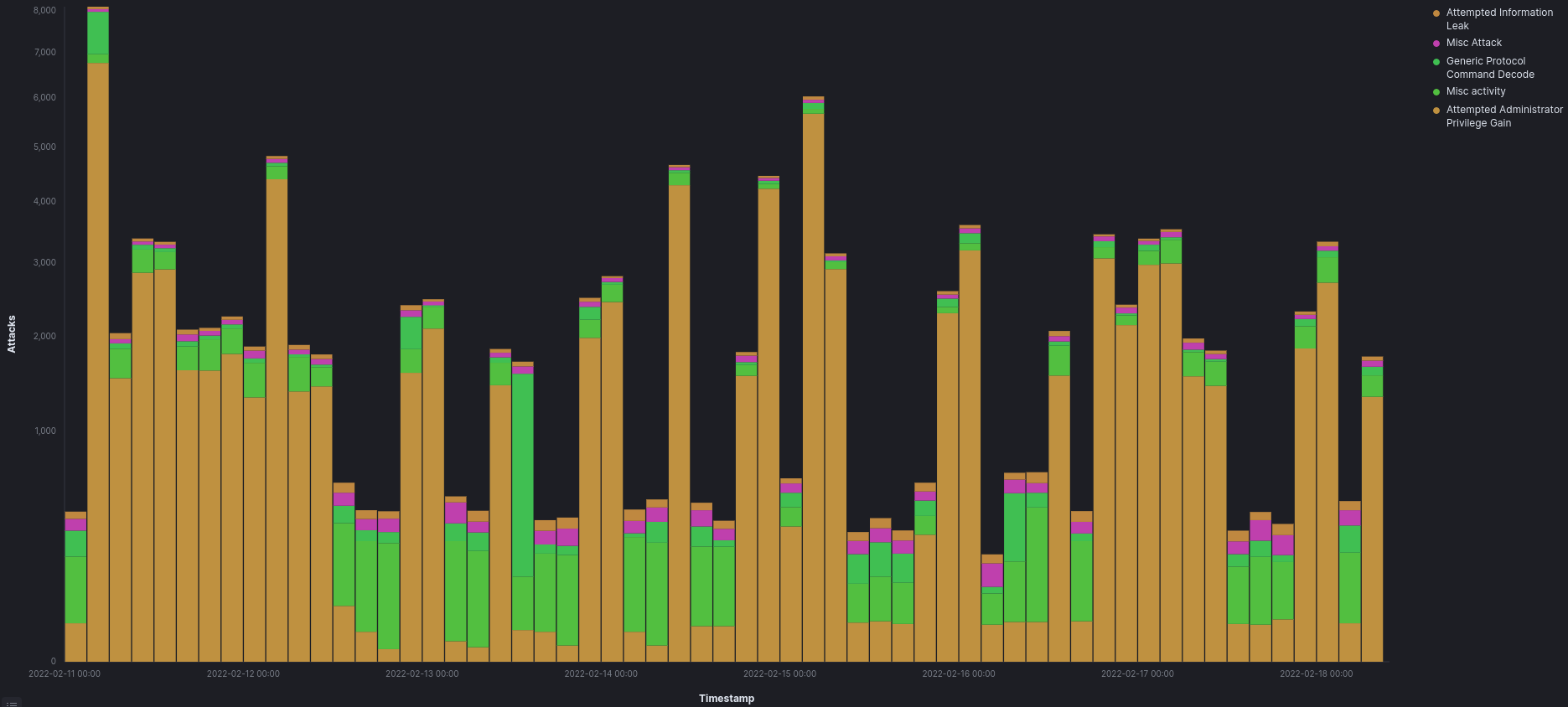
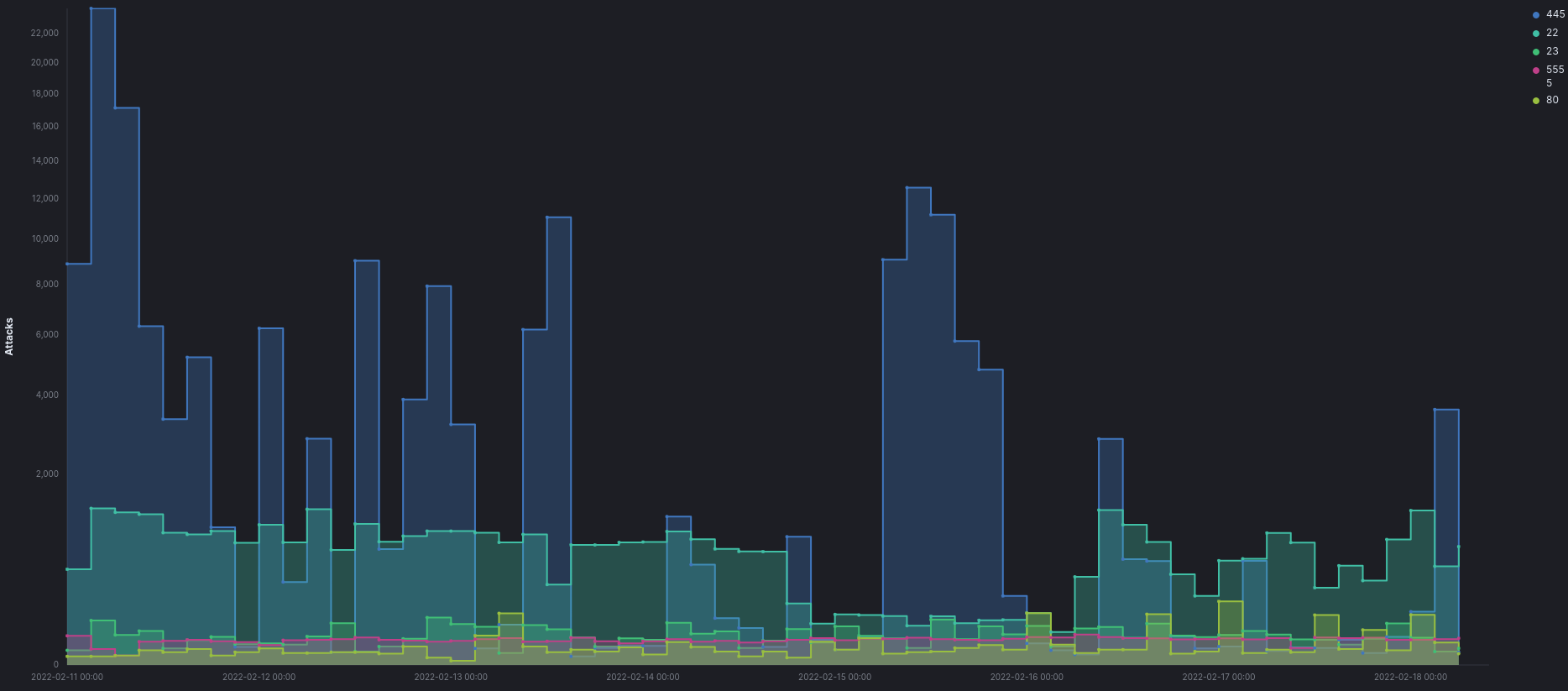
Top Attacks by Destination Port
Top Usernames Attempted

Top Passwords Attempted